某患者,女,19岁。医生的诊断记录是:安氏I2类2分类;毛氏Ⅳ类1分类加I1类1分类。
毛氏Ⅳ类1分类的表现是
A:第一磨牙远中关系,前牙覆 B:第一磨牙近中关系,前牙深覆
B:第一磨牙近中关系,前牙深覆 C:上牙弓宽于下牙弓后牙深覆盖 D:前牙深覆
C:上牙弓宽于下牙弓后牙深覆盖 D:前牙深覆 ,面下1/3过低 E:双颌或双牙弓前突
,面下1/3过低 E:双颌或双牙弓前突
某女性患者,19岁,医生的诊断记录是:安氏Ⅱ类2分类;毛氏Ⅳ类1分类加Ⅰ类1分类。
毛氏Ⅳ类1分类的表现是
A:第一磨牙远中关系,前牙覆 B:第一磨牙近中关系,前牙深覆
B:第一磨牙近中关系,前牙深覆 C:上牙弓宽于下牙弓、后牙深覆盖 D:前牙深覆
C:上牙弓宽于下牙弓、后牙深覆盖 D:前牙深覆 ,面下1/3过低 E:颌或双牙弓前突
,面下1/3过低 E:颌或双牙弓前突
某患者,女,19岁。医生的诊断记录是:安氏Ⅱ类2分类;毛氏Ⅳ类1分类加Ⅰ类1分类。
毛氏Ⅳ类1分类的表现是
A:第一磨牙远中关系,前牙覆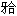 B:第一磨牙近中关系,前牙深覆
B:第一磨牙近中关系,前牙深覆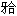 C:上牙弓宽于下牙弓后牙深覆盖 D:前牙深覆
C:上牙弓宽于下牙弓后牙深覆盖 D:前牙深覆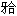 ,面下1/3过低 E:双颌或双牙弓前突
,面下1/3过低 E:双颌或双牙弓前突
(1) is used to ensure the confidentiality, integrity and authenticity of the two end points in the private network. (2) , an application-layer protocol, authenticates each peer in an IPsec transaction. IKE negotiates security policy, determining which algorithm may be used to set up the tunnel. It also handles the exchange of session keys used for that one transaction.
Networks that use (3) to secure data traffic can automatically authenticate devices by using (4) , which verify the identities of the two users who are sending information back and forth. IPsec can be ideal way to secure data in large networks that require secure connections among many devices.
Users deploying IPsec can (5) their network infrastructure without affecting the applications on individual computer. The protocol suite is available as a software-only upgrade to the network infrastructure. This alows security to be implemented without costly changes to each computer. Most important, IPsec allows interoperability among different network devices, PCs and other computing systems.
1()
A:Certificate B:Encryption C:Tunnel D:Presentation
(1) is used to ensure the confidentiality,integrity and authenticity of the two end points in the private network. (2) ,an application—layer protocol,authenticates each peer in an IPSec transaction.IKE negotiates security policy,determining which algorithm may be used to set up the tunnel.it alsohandles the exchange of session keys used for that one transaction.
Networks that use (3) to secure data traffic can automatically authenticate devices by using (4) ,which verify the identities of the two users who are sending information back and forth.IPSeccan be ideal way to secure data in large networks that require secure connections among many devices.
Users deploying IPSec can (5) their network infrastructure without affecting the applications on individual computer.The protocol suite is available as a software-only upgrade to the networkinfrastructure.This alows security to be implemented without costly changes to each computer.Mostimportant,IPSec allows interoperability among different network devices,PCs and other computingsystems.
1()
A:Certificate B:Encryption C:Tunnel D:Presentation

下列分析正确的有( )。
(1)2008年出生人口最多的是南京市区
(2)2008年末泰州市区人口与连云港市区人口相差约2300人
(3)2008年人口增加最多的是淮安市区,增加2.27万人
A:0个 B:1个 C:2个 D:3个

2009年1~10月,该市对俄罗斯的出口金额比2008年同期约净增多少亿美元?( )
A:0.8 B:1 C:3.2 D:3.4
